Centrify Express Smart Card
Most realistic mods for sims 4. Individuals who have a valid authorized need to access DoD Public Key Infrastructure (PKI)- protected information but do not have access to a government site or government-furnished equipment will need to configure their systems to access PKI-protected content.
- Centrify Express For Smart Card
- Centrify Express Smart Card
- Centrify Express For Mac Smart Card
- Centrify Express For Smart Card
Accessing DoD PKI-protected information is most commonly achieved using the PKI certificates stored on your Common Access Card (CAC). The certificates on your CAC can allow you to perform routine activities such as accessing OWA, signing documents, and viewing other PKI-protected information online. For more information about your CAC and the information stored on it, visit http://www.cac.mil.
Before you begin, make sure you know your organization’s policies regarding remote use.
Windows
To get started you will need:
Centrify: Smart Card Support for Macs in Active Directory Environments. Centrify is most known for developing Direct Control, a product that extends Microsoft’s Active Directory to include group policy management of non-Windows servers and workstations.
- CAC
- Card reader
- Middleware (if necessary, depending on your operating system version)
Centrify Express For Smart Card
You can get started using your CAC by following these basic steps:
- Insert your card into the smart card reader. From the Finder, open Applications, then open the Utilities folder and double-click Keychain Access. In the list of Keychains on the left, select the keychain entry for the smart card. The keychain entry is typically labeled as CAC or PIV with a unique number and is usually listed first.
- This group policy modifies /etc/pam.d/system-auth on Red Hat Enterprise Linux 5.6 and /etc/pam.d/smartcard-auth and /etc/pam.d/gnome-screensaver on Red Hat Enterprise Linux 6.0 in order to look for a smart card user’s credentials in Active Directory and verify the identity of the user with the smart card certificate.
- Get a card reader.
At this time, the best advice for obtaining a card reader is to work with your home component to get one. In addition, please review the DoD CAC Reader Specifications for more information regarding the requirements for a card reader. - Install middleware, if necessary.
You may need additional middleware, depending on the operating system you use. Please contact your CC/S/A for more information on the middleware requirements for your organization. You can find their contact information on our Contact Us tab. - Install DoD root certificates with InstallRoot (32-bit, 64-bit or Non Administrator).
In order for your machine to recognize your CAC certificates and DoD websites as trusted, run the InstallRoot utility (32-bit, 64-bit or Non Administrator) to install the DoD CA certificates on Microsoft operating systems. If you’re running an alternate operating system such as Mac OS or Linux, you can import certificates from the PKCS 7 bundle. The InstallRoot User Guide is available here. - Make certificates available to your operating system and/or browser, if necessary.
Pick your browser for specific instructions.
Mac
To get started you will need:
- CAC (see note below)
- Card reader

You can get started using your CAC on your Mac OS X system by following these basic steps:
- Get a card reader
Typically Macs do not come with card readers and therefore an external card reader is necessary. At this time, the best advice for obtaining a card reader is through working with your home component. In addition, please review the DoD CAC Reader Specifications for more information regarding card reader requirements. - Download and install the OS X Smartcard Services package
The OS X Smartcard Services Package allows a Mac to read and communicate with a smart card. In order for your machine to recognize your CAC certificates and DoD websites as trusted, the installer will load the DoD CA certificates on OS X. Please refer to this page for specific installation instructions. - Address the cross-certificate chaining Issue
These instructions walk through adjusting the trust settings on the Interoperability Root CA (IRCA) > DoD Root CA 2 and the US DoD CCEB IRCA 1 > DoD Root CA 2 certificates to prevent cross-certificate chaining issues. This can make it appear that your certificates are issued by roots other than the DoD Root CA 2 and can prevent access to DoD websites. - Configure Chrome and Safari, if necessary
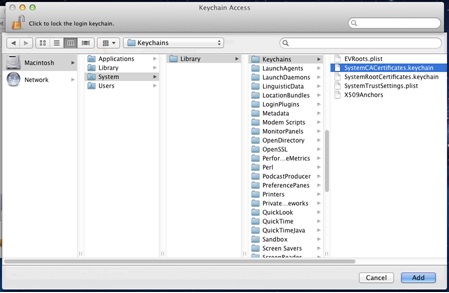
Safari and Google Chrome rely on Keychain Access properly recognizing your CAC certificates.- In Finder, navigate to Go > Utilities and launch KeychainAccess.app
- Verify that your CAC certificates are recognized and displayed in Keychain Access
Centrify Express Smart Card
Note: CACs are currently made of different kinds of card stock. To determine what card stock you have, look at the back of your CAC above the magnetic strip. Most CACs are supported by the Smartcard Services package, however Oberthur ID One 128 v5.5 CACs are not. Third party middleware is available that will support these CACS; two such options are Thursby Software’s PKard and Centrify’s Express for Smart Card.
Linux
To get started you will need:
- CAC
- Card reader
- Middleware
You can get started using your CAC with Firefox on Linux machines by following these basic steps:

- Get a card reader.
At this time, the best advice for obtaining a card reader is to work with your home component to get one. In addition, please review the DoD CAC Reader Specifications for more information regarding the requirements for a card reader. - Obtain middleware.
You will need middleware for Linux to communicate with the CAC. The CoolKey PKCS#11 module provides access to the CAC and can be installed using Linux package management commands.- For Debian-based distributions, use the command apt-get install coolkey
- For Fedora-based distributions, use the command yum install coolkey. The CoolKey PKCS #11 module version 1.1.0 release 15 ships with RHEL 5.7 and above and is located at /usr/lib/pkcs11/libcoolkeypk11.so.
If you prefer to build CoolKey from source, instructions are included in the Configuring Firefox for the CAC guide.
- Configure Firefox to trust the DoD PKI and use the CAC.
To configure Firefox to communicate with the CAC, follow these steps to install the DoD root and intermediate CA certificates into the Firefox NSS trust store, load the CoolKey library, and ensure the Online Certificate Status Protocol (OCSP) is being used to perform revocation checking.
Next Steps
Your internet browser is now configured to access DoD websites using the certificates on your CAC. Now that your machine is properly configured, please login and visit our End Users page for more information on using the PKI certificates on your CAC.
Please select a browser below to access instructions for configuring your browser to use the certificates on your CAC.
IE and Chrome
First check whether your certificates are already available to your browser.
For Internet Explorer 8.0 and above:
- Navigate to Tools > Internet Options > Content and click Certificates.
- On the Personal tab, review the list of certificates to determine if your CAC certificates are in the list. The certificates on your CAC will be issued by a DoD CA.
- If the certificates appear in the list, you are finished. If the certificates do not appear in the list, please see the note below.
For Google Chrome:
- Navigate to Tools > Options > Under the Hood and click Manage Certificates in the HTTPS/SSL section.
- On the Personal tab, review the list of certificates to determine if your CAC certificates are in the list. The certificates on your CAC will be issued by a DoD CA.
- If the certificates appear in the list, you are finished. If the certificates do not appear in the list, please see the note below.
NOTE: If your certificates are not in the list and you’re using ActivClient, please make sure it is installed correctly. If your certificates are not in the list and you are using other middleware, you can contact your CC/S/A for more information on the middleware requirements for your organization. You can find their contact information on our Contact Us tab.
Firefox
Below are complete instructions for using Firefox with your CAC. You may also download these instructions.
Install Certificates from InstallRoot
- Download and install the InstallRoot tool following the instructions in the InstallRoot User Guide or watch this video to learn how:
- Open the InstallRoot tool and select Firefox/Mozilla/Netscape from the Select Trust Store picklist at the bottom of the window.
- Ensure only the top Install DoD NIPRNET Certificates box is checked.
- Click the Install button and wait for the installation to complete. Please wait until you see a confirmation dialog indicating the tool is finished.
- Open Firefox
- Click on Tools > Options in the menu bar.
- In the Options window, go to Advanced > Encryption > Security Devices.
- In the new window, click on Load.
- Enter “ActivClient(CAC)” for the Module Name.
Click Browse to the right of the Module Filename field. Browse to the location of the ActivClient PKCS11 library, acpkcs211.dll. This is typically located at C:Program Files (x86)ActivIdentityActivClientacpkcs211.dll in ActivClient 6.2, and C:Windowssystem32acpkcs201-ns.dll in ActivClient 6.1 and earlier.
Click OK, and then OK again in the confirmation window.
- The confirmation message will show that the security device (CAC) was loaded. CAC certificates can now be used with the browser. Click OK to close the window.
- Open Firefox
- Click on Tools > Options in the menu bar.
- In the Options window, go to Advanced > Encryption > Validation.
- Ensure the option Use the OCSP to confirm the current validity of certificates is checked. Also ensure When an OCSP server connection fails, treat the certificate as invalid is checked.
Using Common Access Card (CAC) certificates in Firefox
These instructions will enable ActivIdentity’s ActivClient software to work within Firefox. Before proceeding, try to ensure the latest version of ActivClient is installed by going to the ActivClient website to check the latest version. Before installing the latest version, please uninstall any previous versions of ActivClient.
As of version 6.2, ActivClient by default configures Firefox to accept the CAC certificates without any additional configuration. You may use the following instructions to verify that it has been installed properly. If using an older version of ActivClient, these instructions will assist with proper configuration.
Ensure the Online Certificate Status Protocol (OCSP) is Performing Revocation Checking
With any versions of ActivClient later than 6.2, these settings will be automatically configured. However, these instructions can be used to confirm proper configuration for older versions of ActivClient.
Super mario 3d world for mac. Safari
To get started you will need:
Centrify Express For Mac Smart Card
- CAC (see note below)
- Card reader
You can get started using your CAC on your Mac OS X system by following these basic steps:
- Get a card reader
Typically Macs do not come with card readers and therefore an external card reader is necessary. At this time, the best advice for obtaining a card reader is through working with your home component. In addition, please review the DoD CAC Reader Specifications for more information regarding card reader requirements. - Download and install the OS X Smartcard Services package
The OS X Smartcard Services Package allows a Mac to read and communicate with a smart card. In order for your machine to recognize your CAC certificates and DoD websites as trusted, the installer will load the DoD CA certificates on OS X. Please refer to this page for specific installation instructions. - Address the cross-certificate chaining Issue
These instructions walk through adjusting the trust settings on the Interoperability Root CA (IRCA) > DoD Root CA 2 and the US DoD CCEB IRCA 1 > DoD Root CA 2 certificates to prevent cross-certificate chaining issues. This can make it appear that your certificates are issued by roots other than the DoD Root CA 2 and can prevent access to DoD websites. - Configure Chrome and Safari, if necessary
Safari and Google Chrome rely on Keychain Access properly recognizing your CAC certificates.- In Finder, navigate to Go > Utilities and launch KeychainAccess.app
- Verify that your CAC certificates are recognized and displayed in Keychain Access
Centrify Express For Smart Card
Note: CACs are currently made of different kinds of card stock. To determine what card stock you have, look at the back of your CAC above the magnetic strip. Most CACs are supported by the Smartcard Services package, however Oberthur ID One 128 v5.5 CACs are not. Third party middleware is available that will support these CACS; two such options are Thursby Software’s PKard and Centrify’s Express for Smart Card.